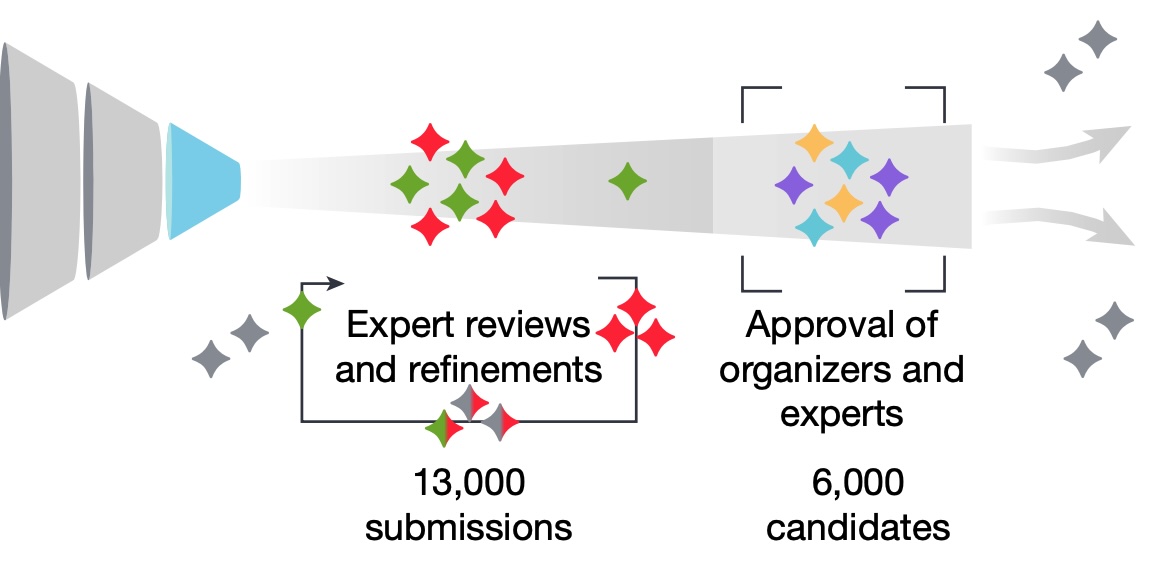
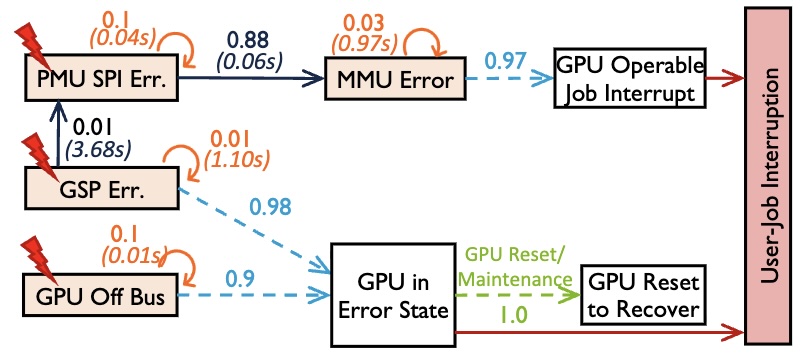
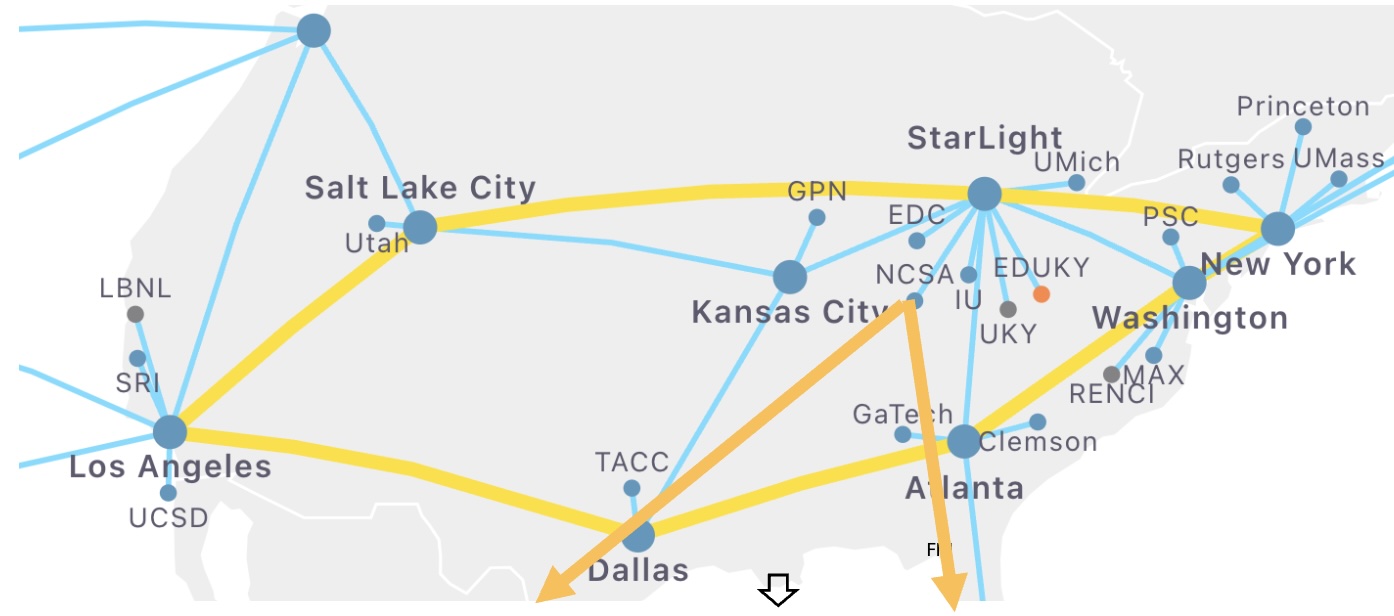
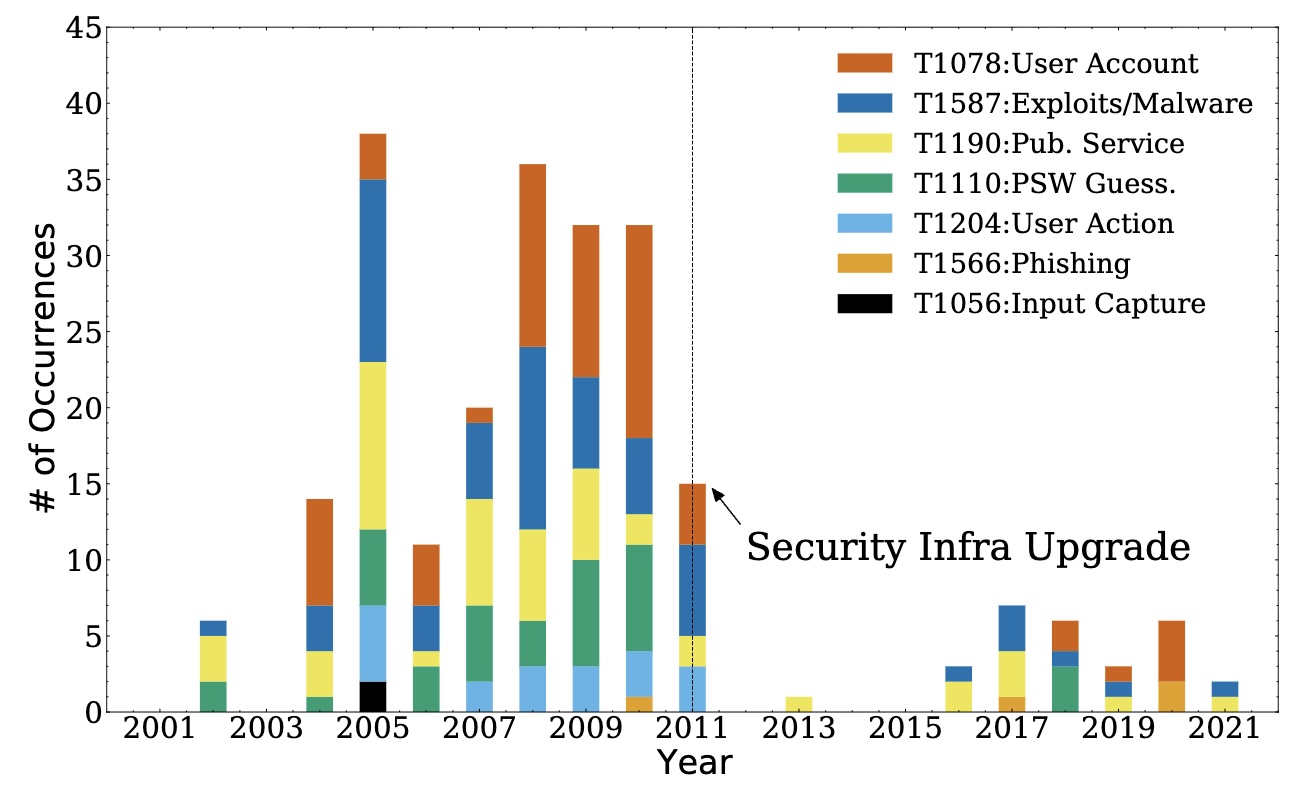
Fellow, National Science Foundation (NSF) Cybersecurity Center of Excellence (TrustedCI)
Center for Artificial Intelligence Innovation
| 2026 |
Program Committee: Intl Conference on Supercomputing (ICS) Quantum Computing and Engineering (QCE) Dependable Systems and Networks (DSN) |
| 2025- |
Reviewer: Department of Energy (DOE) National Artificial Intelligence Research Resource (NAIRR) Pilot |
| 2023- |
Proposal Panelist: National Science Foundation (NSF) |
| 2025 | Steven Ashby Prize in Computational Science, Honorable Mention |
| 2024 | Art of HPC exhibit at the International Conference for High Performance Computing, Networking, Storage and Analysis (SC) |
| 2024 | Jerry Fiddler Innovation Award, Outstanding Mentor |
| 2023 |
Trusted Cyber Infrastructure (CI) Fellows, U.S. National Science Foundation (NSF) Cybersecurity Center of Excellence |
| 2023 |
Best Paper Award, 44th IEEE/IFIP International Conference on Dependable Systems and Networks (DSN) |
| May 2026 |
Joint Laboratory for Extreme Scale Computing Jülich Supercomputing Centre, Germany |
| Apr 2026 |
Trusted CI Regional Cybersecurity Summit
University of Alabama Tuscaloosa, AL |
| Feb 2026 |
Research Security
Academic Security and Counter Exploitation College Station, TX |
| Feb 2026 |
NSF CC* PI Meeting
The Quilt New Orleans, LA |
| Nov 2025 |
Characterizing GPU Resilience on AI/HPC Supercomputing, St. Louis, MO |
| Oct 2025 |
Post Quantum Cryptography Risk in Science National Center for Atmospheric Research Boulder, CO |
| Oct 2025 |
Security Data Lake in Cyberinfrastructure National Institute of Standards and Technology Rockville, MD |
| Nov 2024 |
Jupyter Notebook Security Taxonomy Supercomputing, Atlanta, GA |
| Oct 2023 |
Security Log Analyses Berkeley Lab, CA |
| Nov 2025 |
Two NSF awards granted to NCSA scientist... Grainger Engineering |
| Oct 2025 |
Archit named MLCommons Rising Star for breakthrough GPU research Archit Patke, Illinois ECE |
| Trusted CI Fellow | NSF Cybersecurity Center of Excellence |
| Member | Joint Laboratory for Extreme Scale Computing (JLESC) |
| Member | Quantum Technical Community, IEEE Computer Society |
| Member | ACM SIGHPC |
| Member | SIAM |
| Joel Jothiprakasam | → | JPL |
| Neil Rayu | → | Sandia |
| Advaith Yeluru | → | Microsoft |
| Hung Nguyen | → | Argonne |
| Jakub Sowa | → | KPMG → Undisclosed |
| Edo Giusto | → | University of Naples Federico II; Helix42 |


 Any subjective views or opinions that might be expressed on this page do not necessarily represent the views of the U.S. Department of Energy or the United States Government.
Any subjective views or opinions that might be expressed on this page do not necessarily represent the views of the U.S. Department of Energy or the United States Government.
1205 W. Clark St.
Urbana, IL 61801
Direction

Email: pcao3@illinois.edu
Phuong Cao is a scientist at the National Center for Supercomputing Applications (NCSA) at the University of Illinois at Urbana-Champaign. His research focuses on securing AI for science by building dependable supercomputers. He is a U.S. National Science Foundation (NSF) Trusted Cyberinfrastructure (Trusted CI) Fellow, an affiliate of the Center for Artificial Intelligence Innovation, and a member of the Joint Laboratory for Extreme Scale Computing (JLESC).
Awarded Grants
He is leading a research portfolio as the Principal Investigator of NSF and industry grants, e.g., Cybersecurity Innovation for Cyberinfrastructure (CICI: Security Data Lake), Research on Research Security (RoRS: Uncover HPC allocation abuses), and Formal Method in the Fields (FMiTF: Formalizing Federated Authentication); HPC-Quantum Computing observability (PQSee.com) is being commercialized through initial support of Campus Cyberinfrastructure (CC*: Post Quantum Cryptography Network Instrument). As a fellow of the NSF Cybersecurity Center of Excellence, he provides resiliency expertise to industry partners (IBM Research), mid-scale national testbeds (FABRIC), and DOE national labs.
Honors
Phuong Cao has been recognized with awards for his teaching and mentorship, including a IEEE Dependable Systems and Networks Best Paper Award (2014), Outstanding Mentor for CyberCorps®: Scholarship for Service and Fiddler Innovation Fellowship recipients (2025), and Art of HPC exhibit at Supercomputing 2024. Originally from Vietnam, he is currently a U.S. Permanent Resident (EB1).

Research Agenda
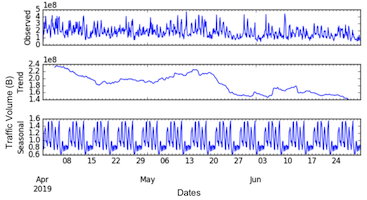
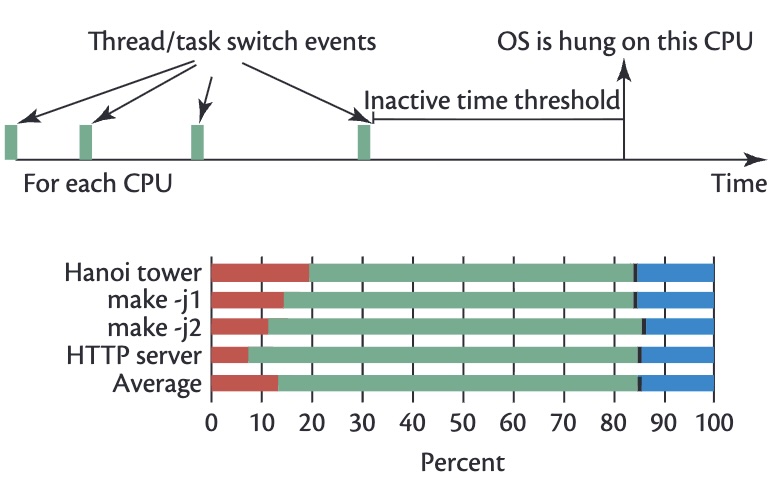
Realizing resilient and secure supercomputing systems to advance open-science research, in the presence of accidental failures and cyber-attacks is his research goal. The key driver is cross-stack measurements of high-speed interconnects, AI application logs, and kernel probes from sustained petascale supercomputers (Blue Waters), HPC/GPU clusters (DeltaAI. These decade-long curated data (1PB) enables cyberattack detection, error propagation modeling across GPU architectures (Hopper/Blackwell/Rubin) and vendors, and understanding of quantum-resistant cryptography adoption, published in top conferences such as Supercomputing, USENIX Security, and IEEE Quantum Computing and Engineering. He is investigating reliability and security challenges of next-generation accelerators such as Quantum Processing Units (QPU) being integrated with HPC.
Research Thrusts
- Reliability of Computing Accelerators, e.g., Graphics Processing Units (GPU), Quantum Processing Units (QPU), and HPC-QC integration from petascale to exascale.
- Security Measurements of High-performance Networking Facilities, e.g., NCSA and FABRIC testbed for open-science research, extending to Internet-scale measurements.
- Research Security, e.g., security auditing of HPC allocations, research security education, and policies.
Center for AI Safety, Scale AI & HLE Contributors Consortium
Nature
Shengkun Cui, Archit Patke, Hung Nguyen, Aditya Ranjan, Ziheng Chen,
Phuong Cao, Brett Bode, Gregory Bauer, Catello Di Martino, Saurabh Jha, Chandra Narayanaswami, Daby Sow, Zbigniew Kalbarczyk, Ravishankar Iyer
Supercomputing '25
Measuring PQC Adoption Rates and Identifying Migration Pathways
Jakub Sowa, Bach Hoang, Advaith Yeluru, Steven Qie, Anita Nikolich, Ravishankar Iyer, Phuong M. Cao
IEEE International Conference on Quantum Computing and Engineering (QCE)
Limin Yang, Zhi Chen, Chenkai Wang, Zhenning Zhang, Sushruth Booma, Phuong M. Cao, Constantin Adam, Alex Withers, Zbigniew Kalbarczyk, Ravishankar K. Iyer, Gang Wang
33rd USENIX Security Symposium
Keywhan Chung, Phuong M. Cao, Zbigniew Kalbarczyk, Ravishankar K Iyer
IEEE International Conference on Cyber Security and Resilience, 2023
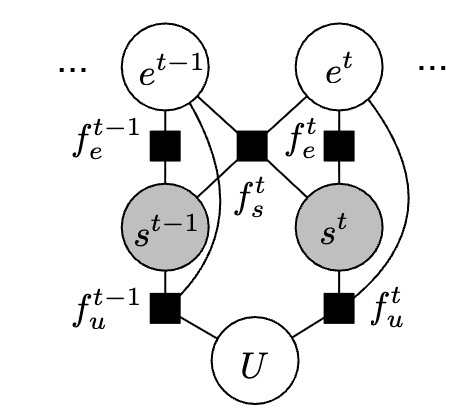
Shuo Chen, Matt McCutchen, Phuong M. Cao, Shaz Qadeer, and Ravishankar Iyer
International Conference on Runtime Verification (RV), 2017
Workshops, Short Papers, and Magazine Articles
Yurui Cao, Phuong M. Cao, Haotian Chen, Karl M. Kochendorfer, Andrew B. Trotter, William L. Galanter, Paul M. Arnold, Ravishankar K Iyer
AAAI-22 Health Intelligence Workshop
Phuong M. Cao, Bach Hoang, Santiago Nunez-Corrales
ASCR Workshop on Basic Research Needs in Quantum Computing and Networking, Department of Energy, (Position Paper), 2023.
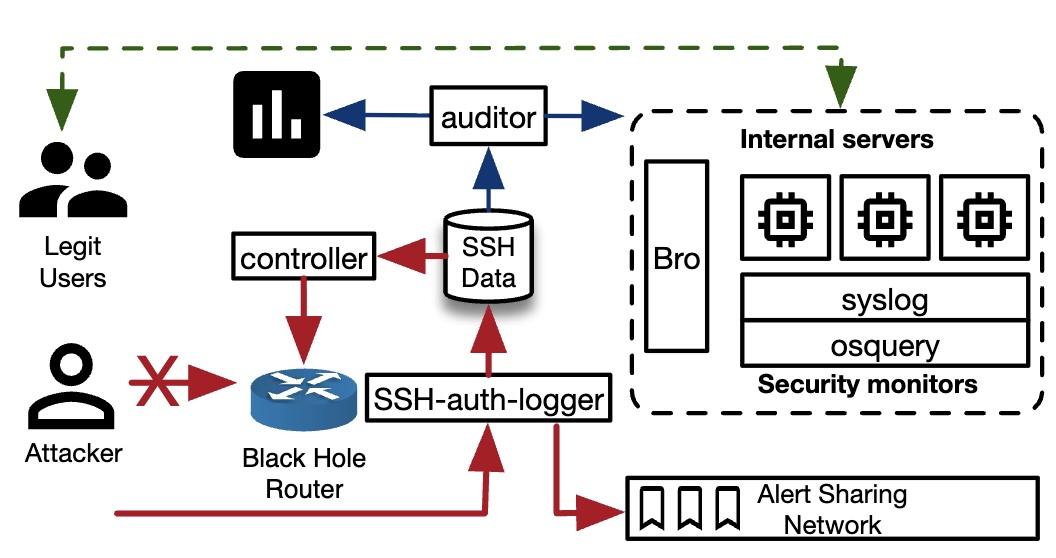
Jim Basney, Phuong M. Cao, Terry Fleury
IEEE DependSys 2020
Yuming Wu, Phuong M. Cao, Alex Withers, Zbigniew Kalbarczyk, Ravishankar Iyer
Workshop on Decentralized IoT Systems and Security, co-located with NDSS, 2020
Vanessa Tay, Xinran Li, Daisuke Mashima, Bennet Ng, Phuong M. Cao, Zbigniew Kalbarczyk, Ravishankar K Iyer
IEEE International Conference on Smart Grid Communications (SmartGridComm), 2023